Market Definition
Zero trust security is a strategic cybersecurity framework that eliminates implicit trust in users, devices, or networks, requiring continuous verification for access to critical business resources. It enforces strict identity authentication, least-privilege access, and network segmentation to minimize risk, prevent unauthorized access, and strengthen organizational resilience against modern cyber threats.
Zero Trust Security Market Overview
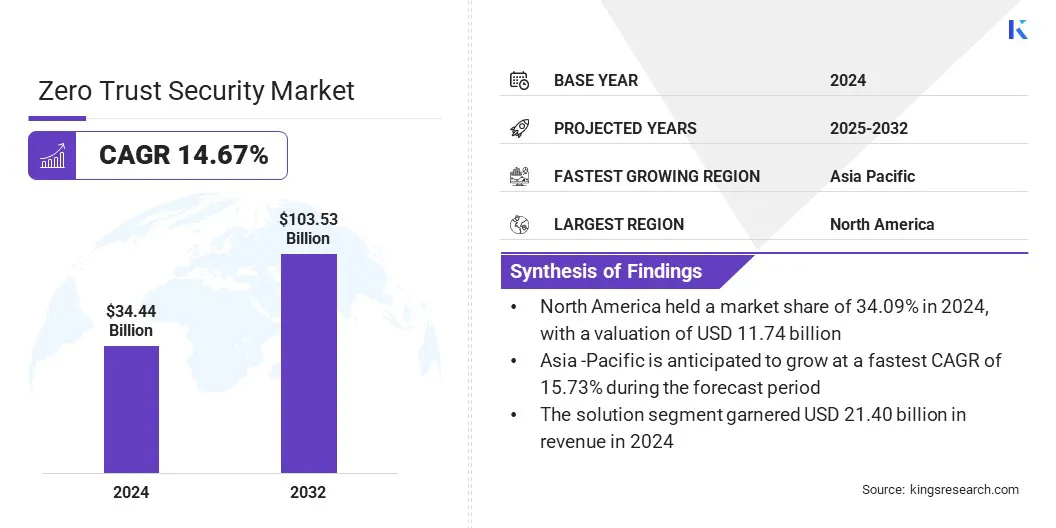
The global zero trust security market size was valued at USD 34.44 billion in 2024 and is projected to grow from USD 39.38 billion in 2025 to USD 103.53 billion by 2032, exhibiting a CAGR of 14.67% during the forecast period. This growth is driven by the increasing frequency and sophistication of cyberattacks, prompting organizations to adopt advanced security frameworks to safeguard sensitive data and maintain business continuity.
Additionally, the shift toward cloud infrastructure and distributed workforces is increasing demand for secure access solutions that protect users, devices, and applications across diverse and remote environments.
Key Highlights:
- The zero trust security industry size was recorded at USD 34.44 billion in 2024.
- The market is projected to grow at a CAGR of 14.67% from 2025 to 2032.
- North America held a share of 34.09% in 2024, valued at USD 11.74 billion.
- The solution segment garnered USD 21.40 billion in revenue in 2024.
- The on-premises segment is expected to reach USD 61.05 billion by 2032.
- The single-factor segment is anticipated to witness the fastest CAGR of 14.93% over the forecast period.
- The data security segment held a share of 27.44% in 2024
- The BFSI segment garnered USD 29.90 billion in revenue in 2024
- Asia Pacific is anticipated to grow at a CAGR of 15.73% over the forecast period.
Major companies operating in the zero trust security market are Cisco Systems, Inc, Microsoft, Palo Alto Networks, Inc, Broadcom, Zscaler, Inc, Cloudflare, Inc, Fortinet, Inc, Check Point Software Technologies Ltd, Akamai Technologies, Netskope, Inc, IBM Corporation, Kyndryl Inc, Okta, Inc, StrongDM, Inc, and BeyondTrust Corporation.
Rising adoption of cloud computing and remote work is prompting organizations to secure access across hybrid and multi-cloud IT environments. Enterprises are deploying zero trust frameworks to enforce identity-based access, continuous monitoring, and protect sensitive data from unauthorized access and insider threats.
- In October 2024, Alkira launched its cloud-based Zero Trust Network Access (ZTNA) solution to provide end-to-end secure connectivity for enterprises. The platform combines zero trust principles with network infrastructure expertise to deliver granular, identity-based access and optimized performance across multi-cloud and remote environments.
Market Driver
Growing Awareness of Insider Threats
The growth of the zero trust security market is propelled by the growing awareness of insider threats and risks from employees, contractors, or third-party partners compromising sensitive information.
Organizations are implementing zero trust frameworks that enforce strict identity verification, least-privilege access, and continuous monitoring to prevent unauthorized access and data breaches. This focus on internal security and proactive threat mitigation is prompting enterprises to adopt zero trust strategies across IT and operational sectors.
- In August 2024, the Cybersecurity and Infrastructure Security Agency (CISA) reported that the average cost of an insider threat incident increased to USD 16.2 million per organization in 2023, highlighting the urgent need for robust security frameworks such as Zero Trust.
Market Challenge
High Implementation and Integration Costs
A key challenge impeding the progress of the zero trust security market is the high implementation and integration costs associated with deploying comprehensive security frameworks.
Zero trust solutions require advanced technologies such as identity and access management systems, network segmentation tools, continuous monitoring platforms, and endpoint security solutions, which can result in substantial upfront investment. This initial financial burden can deter small and medium-sized enterprises from adopting zero trust security solutions.
To address this challenge, market players are offering modular, cloud-based, and as-a-service solutions that reduce upfront investment and simplify the deployment of zero trust frameworks across IT and operational sectors.
Vendors are providing scalable deployment models, subscription-based pricing, and pre-integrated platforms to simplify adoption and lower financial barriers. Additionally, companies are investing in professional services, training, and automated tools to streamline integration with existing IT infrastructure.
Market Trend
Expansion of Zero Trust into IoT and Operational Technology
A key trend influencing the zero trust Security market is the expansion of zero trust principles into IoT and operational technology environments to secure connected devices, industrial equipment, and distributed networks.
Market players are developing solutions that isolate endpoints, enforce continuous authentication, and monitor device behavior to prevent unauthorized access and lateral threat movement. This approach is enabling broader adoption of zero trust in industrial, manufacturing, and critical infrastructure settings. These innovations are helping organizations safeguard mission-critical operations while enhancing resilience and operational security.
- In July 2025, Zscaler extended its Zero Trust Exchange platform with Zscaler Cellular, enabling secure Zero Trust communication for IoT and OT devices using only a SIM card. The solution eliminates the need for VPNs or additional software, isolates each device to reduce attack surfaces, and ensures resilient, cloud-managed connectivity across global cellular networks.
Zero Trust Security Market Report Snapshot
|
Segmentation
|
Details
|
|
By Component
|
Solution, Services
|
|
By Deployment
|
Cloud-based, On-premises
|
|
By Authentication
|
Single-factor, Multi-factor
|
|
By Type
|
Network Security, Data Security, Cloud Security, Endpoint Security, Others
|
|
By Vertical
|
BFSI, IT & Telecommunications, Retail, Government, Healthcare, Others
|
|
By Region
|
North America: U.S., Canada, Mexico
|
|
Europe: France, UK, Spain, Germany, Italy, Russia, Rest of Europe
|
|
Asia-Pacific: China, Japan, India, Australia, ASEAN, South Korea, Rest of Asia-Pacific
|
|
Middle East & Africa: Turkey, U.A.E., Saudi Arabia, South Africa, Rest of Middle East & Africa
|
|
South America: Brazil, Argentina, Rest of South America
|
Market Segmentation:
- By Component (Solution and Services): The solution segment earned USD 21.40 billion in 2024, mainly due to rising adoption of comprehensive zero trust frameworks and increasing demand for integrated security solutions.
- By Deployment (Cloud-based and On-premises): The on-premises segment held a share of 59.94% in 2024, fueled by enterprises relying on legacy infrastructure and in-house security management.
- By Authentication (Single-factor and Multi-factor): The single-factor segment is projected to reach USD 57.38 billion by 2032, owing to its simplicity and ease of implementation for basic access control.
- By Type (Network Security, Data Security, Cloud Security, and Endpoint Security): The network security segment is anticipated to witness the fastest CAGR of 15.23% over the forecast period, attributed to increasing cyberattacks on enterprise networks.
- By VERTICAL (BFSI, IT & Telecommunications, Retail, and Government): The BFSI segment garnered USD 10.30 billion in revenue in 2024, propelled by the critical need for secure financial transactions and regulatory compliance.
Zero Trust Security Market Regional Analysis
Based on region, the market has been classified into North America, Europe, Asia Pacific, Middle East & Africa, and South America.
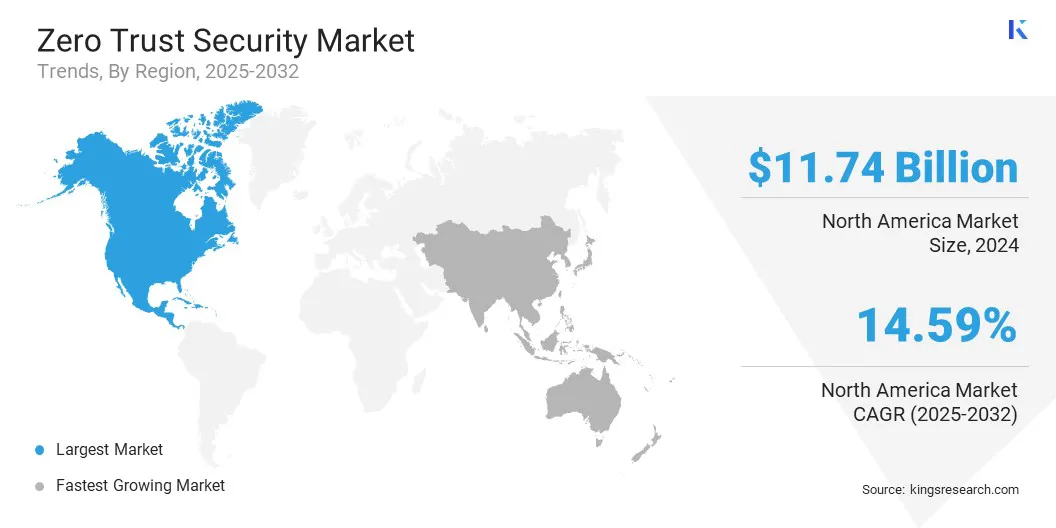
The North America zero trust security market accounted for a share of 34.09% in 2024, valued at USD 11.74 billion. This dominance is reinforced by the increasing frequency and sophistication of cyberattacks, which are compelling organizations to adopt advanced security frameworks to safeguard sensitive data and critical infrastructure.
Rapid digital transformation and widespread adoption of cloud computing and remote work are creating demand for secure access. Stringent regulatory compliance requirements, such as GDPR and CCPA, are enforcing stricter data protection and access control measures. Growing awareness of insider threats is prompting enterprises to implement least-privilege access and continuous monitoring.
Additionally, the expansion of cloud-based and adaptive security solutions by leading technology providers is enabling organizations to strengthen security postures while simplifying deployment and management, fueling regional market growth.
- In April 2025, Hewlett Packard Enterprise (HPE) expanded its Aruba Networking and GreenLake cloud offerings to enhance zero trust security and hybrid cloud operations. These updates introduce cloud-based access controls and threat-adaptive security to protect users, devices, and applications.
The Asia-Pacific zero trust security industry is set to grow at a robust CAGR of 15.73% over the forecast period. This growth is attributed to the rapid adoption of cloud computing and mobile-first business strategies, generating demand for secure and scalable access solutions.
Increasing cyber threats targeting government, financial, and critical infrastructure sectors are prompting organizations to implement advanced zero trust frameworks. Regional regulatory initiatives, such as India’s Digital Personal Data Protection Act and Australia’s Security of Critical Infrastructure Act, are enforcing stricter data privacy and security measures.
Additionally, growing collaboration between local consulting firms and cybersecurity technology providers is helping organizations modernize legacy security models and accelerate zero trust adoption across the region.
- In August 2024, KPMG in India formed a strategic alliance with Zscaler to provide Zero Trust-aligned data security services. The partnership aims to help organizations transition from legacy security models to modern zero trust architectures by offering cloud-delivered protection for endpoints, workloads, identity, and data, while addressing emerging cyber threats and regulatory compliance requirements.
Regulatory Frameworks
- In the U.S., the Cybersecurity and Infrastructure Security Agency (CISA) oversees cybersecurity frameworks, including zero trust adoption, by issuing guidelines, best practices, and mandates for federal agencies and critical sectors. CISA ensures organizations implement strong identity management, access control, and continuous monitoring to mitigate cyber threats.
- In the UK, the National Cyber Security Centre (NCSC) provides guidance and regulation for cybersecurity across government and industry sectors. It monitors the adoption of zero trust strategies by emphasizing identity verification, least-privilege access, and network segmentation. NCSC issues standards, best practices, and threat intelligence to ensure organizations reduce risk and comply with U.K. data protection regulations.
- In China, the Cyberspace Administration of China (CAC) regulates national cybersecurity policies, data protection, and network security standards. It supervises the implementation of secure access controls, identity verification, and monitoring frameworks aligned with zero trust principles for critical information infrastructure. CAC enforces compliance with laws on data localization, cross-border transfer, and cybersecurity risk management across enterprises.
- In India, the Indian Computer Emergency Response Team (CERT-In) acts as the national authority for cybersecurity incident management and regulatory guidance. It monitors and mandates the adoption of robust security measures, including identity authentication, access control, and threat monitoring under zero trust frameworks. CERT-In also issues advisories for organizations to comply with India’s IT Act and data protection rules.
Competitive Landscape
Major players in the zero trust security industry are focusing on strategic partnerships to accelerate the adoption of AI-enabled security solutions. They are prioritizing modernizing and simplifying enterprise security postures through cloud-based zero trust platforms.
Organizations are securing access for users, devices, and applications in hybrid and cloud-first infrastructures. Additionally, they are developing cloud-delivered access controls, implementing zero trust network architectures for hybrid environments, and providing solutions to secure workloads and data across IT infrastructures.
- In December 2024, Cognizant expanded its partnership with Zscaler to accelerate the adoption of AI-enabled Zero Trust security. The collaboration aims to help enterprises modernize and simplify their security posture through a cloud-based Zero Trust platform, enhancing threat detection, policy enforcement, and secure access across hybrid and cloud-first environments.
Key Companies in Zero Trust Security Market:
- Cisco Systems, Inc
- Microsoft
- Palo Alto Networks, Inc
- Broadcom
- Zscaler, Inc
- Cloudflare, Inc
- Fortinet, Inc
- Check Point Software Technologies Ltd
- Akamai Technologies
- Netskope, Inc
- IBM Corporation
- Kyndryl Inc
- Okta, Inc
- StrongDM, Inc
- BeyondTrust Corporation.
Recent Developments (Product Launch)
- In June 2025, Zscaler launched a new suite of Zero Trust solutions under its Zero Trust Everywhere, securing users, devices, applications, branches, and multi-cloud workloads. The suite features AI-driven microsegmentation, Zero Trust gateways, and a B2B Exchange platform, helping organizations prevent lateral threat movement, simplify security infrastructure, and enhance visibility across distributed and hybrid environments.


